wafw00f
总述
WAF(Web Application Firewall,Web 应用防火墙)是一种专门针对 HTTP/HTTPS 流量进行监控和过滤的安全设备或服务,用于保护 Web 应用免受常见的攻击。它工作在应用层(OSI 七层模型中的第七层),能够识别并拦截诸如 SQL 注入、跨站脚本(XSS)、文件包含、远程代码执行等漏洞利用行为。
总而言之,WAF 就是包含站点的一道防火墙,阻断我们渗透攻击者的明显的一些恶意请求(匹配到 waf 当中的一些拦截规则),而存在 waf 那我们的渗透难度当然就增加了许多,这个时候我们就要考虑 waf 绕过了。无论是 语法 上绕过 waf,还是我们直接找到 业务 的 上游真实服务器,都哭呀帮助我们绕过 waf。具体详见 waf 绕过章节文章吧。
神
1. Windows 不好用!!Linux上使用!!
2. json > csv > txt
简介
wafw00f 是一个用来识别 Web 应用防火墙(WAF)产品的开源工具。
使用方法
# 下载
git clone https://github.com/EnableSecurity/wafw00f.git
cd wafw00f
# 安装
(python setup.py -h)
python setup.py install
# 安装完毕,使用
cd wafw00f - (~/wafw00f/wafw00f - 没错是这样的)
python main.py -h
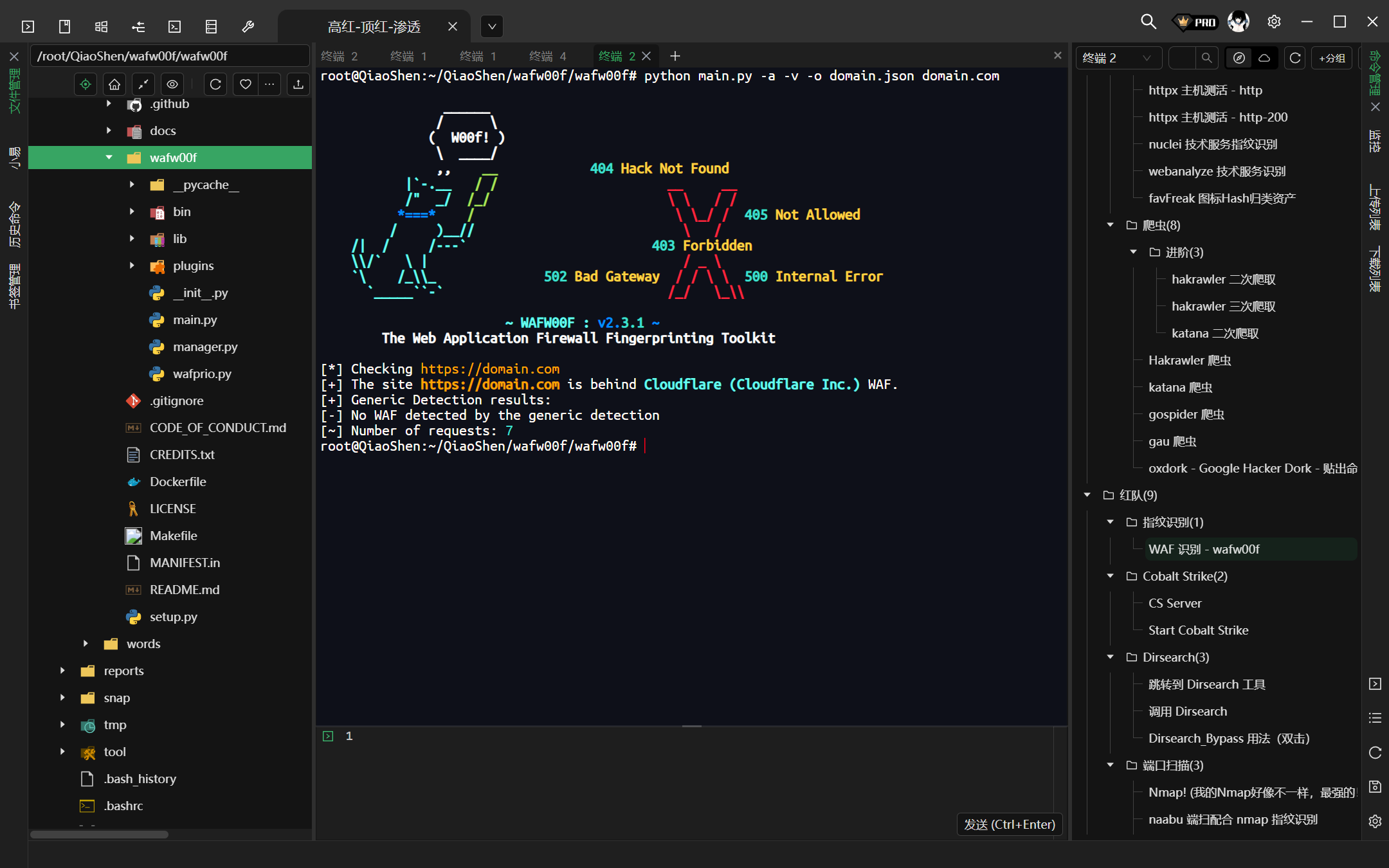
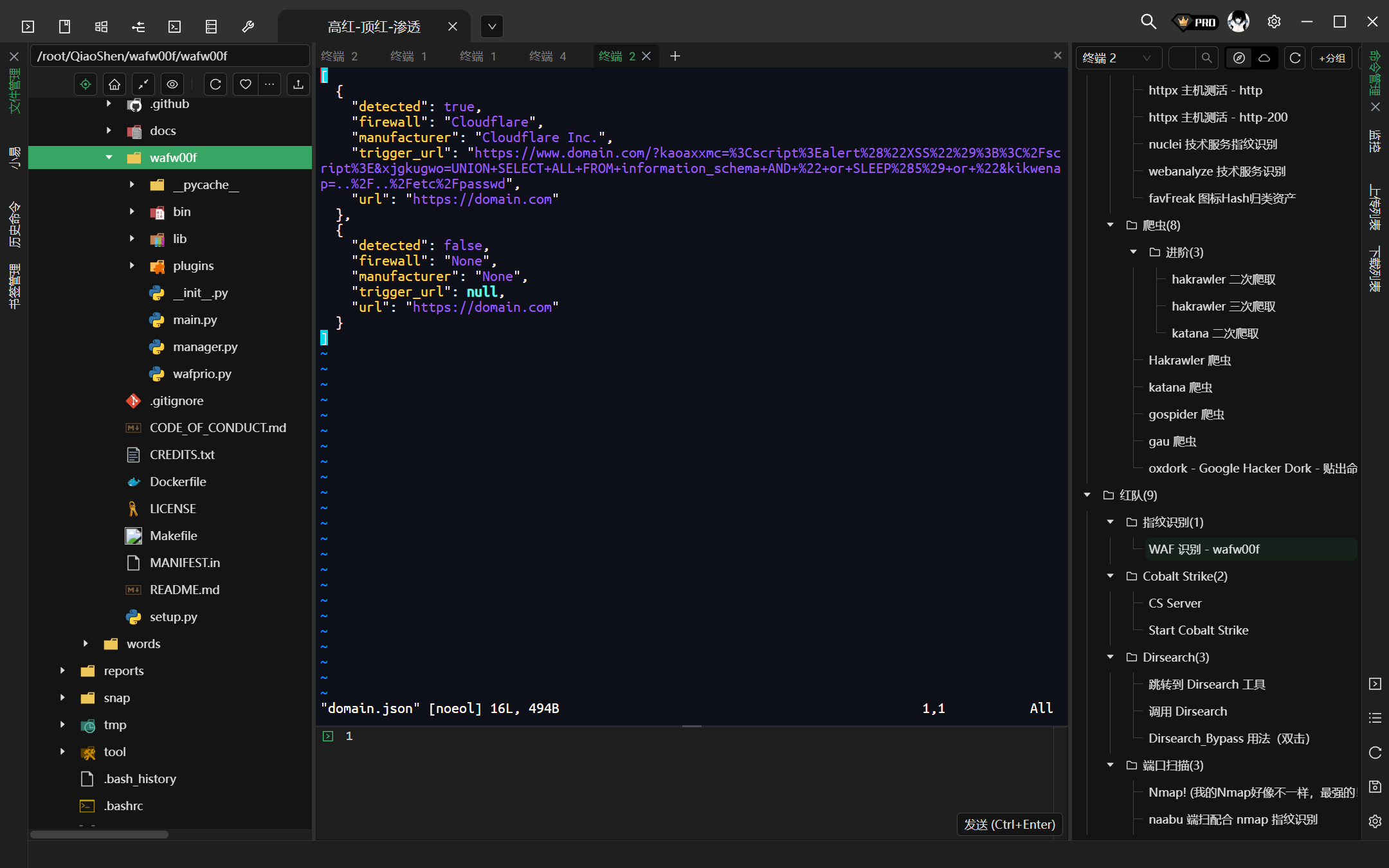
python -a -v -o domain.csv domain.com (https://domain.com - 均可)
-a 发掘该站点上可能存在的所有的 waf 特征 - 对应 waf。
-v 详细模式
-o 结果输出到某文件当中 (csv、json、txt - 但是输出的 waf 结果不是 console 台上的结果,奇怪)
python main.py -h
root@QiaoShen:~/QiaoShen/wafw00f/wafw00f# python main.py -h
Usage: main.py url1 [url2 [url3 ... ]]
example: main.py http://www.victim.org/
Options:
-h, --help show this help message and exit
-v, --verbose Enable verbosity, multiple -v options increase
verbosity
-a, --findall Find all WAFs which match the signatures, do not stop
testing on the first one
-r, --noredirect Do not follow redirections given by 3xx responses
-t TEST, --test=TEST Test for one specific WAF
-o OUTPUT, --output=OUTPUT
Write output to csv, json or text file depending on
file extension. For stdout, specify - as filename.
-f FORMAT, --format=FORMAT
Force output format to csv, json or text.
-i INPUT, --input-file=INPUT
Read targets from a file. Input format can be csv,
json or text. For csv and json, a `url` column name or
element is required.
-l, --list List all WAFs that WAFW00F is able to detect
-p PROXY, --proxy=PROXY
Use an HTTP proxy to perform requests, examples:
http://hostname:8080, socks5://hostname:1080,
http://user:pass@hostname:8080
-V, --version Print out the current version of WafW00f and exit.
-H HEADERS, --headers=HEADERS
Pass custom headers via a text file to overwrite the
default header set.
-T TIMEOUT, --timeout=TIMEOUT
Set the timeout for the requests.
--no-colors Disable ANSI colors in output.
实景演示
# 下载
root@QiaoShen:~/QiaoShen# git clone https://github.com/EnableSecurity/wafw00f.git
Cloning into 'wafw00f'...
remote: Enumerating objects: 5021, done.
remote: Counting objects: 100% (1097/1097), done.
remote: Compressing objects: 100% (265/265), done.
remote: Total 5021 (delta 917), reused 832 (delta 832), pack-reused 3924 (from 3)
Receiving objects: 100% (5021/5021), 807.80 KiB | 1.69 MiB/s, done.
Resolving deltas: 100% (3662/3662), done.
root@QiaoShen:~/QiaoShen# cd wafw00f/
root@QiaoShen:~/QiaoShen/wafw00f# ls
CODE_OF_CONDUCT.md Dockerfile LICENSE MANIFEST.in setup.py
CREDITS.txt docs Makefile README.md wafw00f
# 安装
root@QiaoShen:~/QiaoShen/wafw00f# python setup.py install /usr/local/lib/python3.10/dist-packages/setuptools/dist.py:599: SetuptoolsDeprecationWarning: Invalid dash-separated key 'index-url' in 'easy_install' (setup.cfg), please use the underscore name 'index_url' instead. !! ******************************************************************************** Usage of dash-separated 'index-url' will not be supported in future versions. Please use the underscore name 'index_url' instead. By 2026-Mar-03, you need to update your project and remove deprecated calls or your builds will no longer be supported. See https://setuptools.pypa.io/en/latest/userguide/declarative_config.html for details. ******************************************************************************** !! opt = self._enforce_underscore(opt, section)
...
installing library code to build/bdist.linux-x86_64/egg
running install_lib
running build_py
creating build/lib/wafw00f
copying wafw00f/manager.py -> build/lib/wafw00f
copying wafw00f/__init__.py -> build/lib/wafw00f
copying wafw00f/wafprio.py -> build/lib/wafw00f
copying wafw00f/main.py -> build/lib/wafw00f
creating build/lib/wafw00f/lib
copying wafw00f/lib/asciiarts.py -> build/lib/wafw00f/lib
copying wafw00f/lib/__init__.py -> build/lib/wafw00f/lib
copying wafw00f/lib/evillib.py -> build/lib/wafw00f/lib
...
Using /usr/local/lib/python3.10/dist-packages
Finished processing dependencies for wafw00f==2.3.1
root@QiaoShen:~/QiaoShen/wafw00f# ls
build CREDITS.txt Dockerfile LICENSE MANIFEST.in setup.py wafw00f.egg-info
CODE_OF_CONDUCT.md dist docs Makefile README.md wafw00f
# 使用
root@QiaoShen:~/QiaoShen/wafw00f# cd wafw00f
root@QiaoShen:~/QiaoShen/wafw00f/wafw00f# python main.py -h
Usage: main.py url1 [url2 [url3 ... ]]
example: main.py http://www.victim.org/
Options:
-h, --help show this help message and exit
-v, --verbose Enable verbosity, multiple -v options increase
verbosity
-a, --findall Find all WAFs which match the signatures, do not stop
testing on the first one
-r, --noredirect Do not follow redirections given by 3xx responses
-t TEST, --test=TEST Test for one specific WAF
-o OUTPUT, --output=OUTPUT
Write output to csv, json or text file depending on
file extension. For stdout, specify - as filename.
-f FORMAT, --format=FORMAT
Force output format to csv, json or text.
-i INPUT, --input-file=INPUT
Read targets from a file. Input format can be csv,
json or text. For csv and json, a `url` column name or
element is required.
-l, --list List all WAFs that WAFW00F is able to detect
-p PROXY, --proxy=PROXY
Use an HTTP proxy to perform requests, examples:
http://hostname:8080, socks5://hostname:1080,
http://user:pass@hostname:8080
-V, --version Print out the current version of WafW00f and exit.
-H HEADERS, --headers=HEADERS
Pass custom headers via a text file to overwrite the
default header set.
-T TIMEOUT, --timeout=TIMEOUT
Set the timeout for the requests.
--no-colors Disable ANSI colors in output.
# 使用
root@QiaoShen:~/QiaoShen/wafw00f/wafw00f# python main.py -v -a -o baidu.csv http://baidu.com
______
/ \
( W00f! )
\ ____/
,, __ 404 Hack Not Found
|`-.__ / / __ __
/" _/ /_/ \ \ / /
*===* / \ \_/ / 405 Not Allowed
/ )__// \ /
/| / /---` 403 Forbidden
\\/` \ | / _ \
`\ /_\\_ 502 Bad Gateway / / \ \ 500 Internal Error
`_____``-` /_/ \_\\
~ WAFW00F : v2.3.1 ~
The Web Application Firewall Fingerprinting Toolkit
[*] Checking http://baidu.com
ERROR:wafw00f:Something went wrong ('Connection aborted.', RemoteDisconnected('Remote end closed connection without response'))
[+] Generic Detection results:
[*] The site http://baidu.com seems to be behind a WAF or some sort of security solution
[~] Reason: The server header is different when an attack is detected.
The server header for a normal response is "BWS/1.1", while the server header a response to an attack is "",
[~] Number of requests: 6
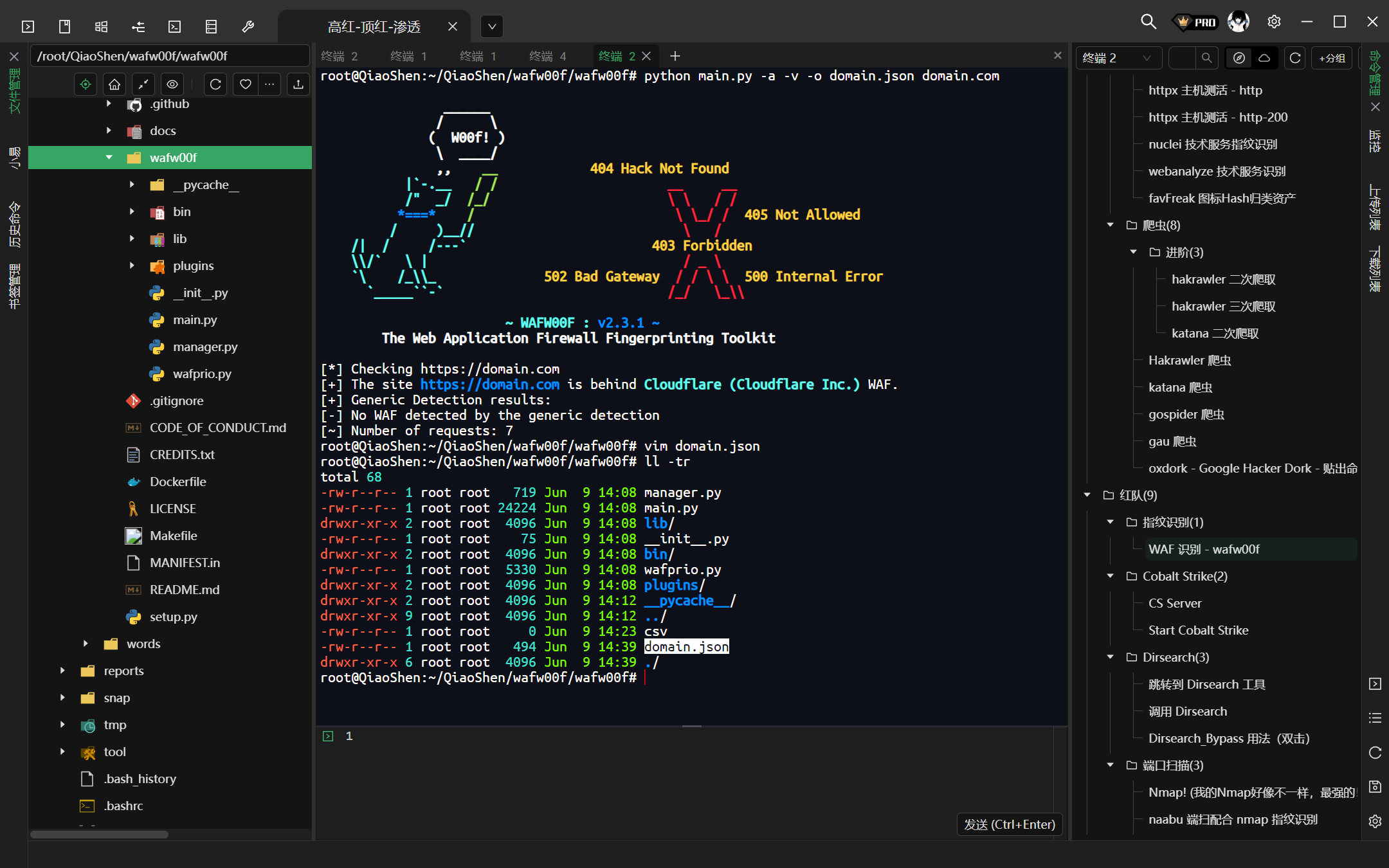
root@QiaoShen:~/QiaoShen/wafw00f/wafw00f# ll -tr
total 68
-rw-r--r-- 1 root root 719 Jun 9 14:08 manager.py
-rw-r--r-- 1 root root 24224 Jun 9 14:08 main.py
drwxr-xr-x 2 root root 4096 Jun 9 14:08 lib/
-rw-r--r-- 1 root root 75 Jun 9 14:08 __init__.py
drwxr-xr-x 2 root root 4096 Jun 9 14:08 bin/
-rw-r--r-- 1 root root 5330 Jun 9 14:08 wafprio.py
drwxr-xr-x 2 root root 4096 Jun 9 14:08 plugins/
drwxr-xr-x 2 root root 4096 Jun 9 14:12 __pycache__/
drwxr-xr-x 9 root root 4096 Jun 9 14:12 ../
-rw-r--r-- 1 root root 0 Jun 9 14:23 csv
-rw-r--r-- 1 root root 92 Jun 9 14:24 baidu.csv <-- 生成的扫描结果
drwxr-xr-x 6 root root 4096 Jun 9 14:24 ./
本文链接:
/archives/wafw00f
版权声明:
本站所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自
QiaoShen-World!
喜欢就支持一下吧
